Introduction
Decentralized applications (DApps) are changing the game. Bringing us into a world of trustless, transparent systems powered by blockchain technology, but with a catch. Even the most decentralized applications have a weak spot, that is their web application components. These centralized elements can jeopardize the very essence of the decentralization that web3 is built on.
Typically, interacting with a dApp involves navigating a web browser, visiting a website, connecting your wallet via a browser extension, and then engaging with the dApp. This interaction is where the weakness lies. In fact, many of last year’s dApp exploits occurred not through blockchain vulnerabilities, but via weaknesses in web2 infrastructure. This revelation is what sparked our mission to enhance security at the intersection of web2 and web3 technologies.
The Catalyst
Last year saw a wave of attacks exploiting the bridge between web2 and web3 (which we lovingly call web2.5), exposing significant vulnerabilities in dApps. Attacks like CDN hijacking, DNS manipulation, and BGP hijacking were particularly rampant. These incidents highlighted critical weaknesses in the web2 infrastructure that dApps depend on.
Here’s a quick breakdown of these attack methods:
What is CDN Hijacking?
Attackers gain unauthorized control over a CDN (Content Delivery Network) used by a WebApp to deliver content such as scripts. By compromising a CDN, they can inject malicious code into the WebApp, potentially stealing funds, capturing user data, or redirecting transactions to unauthorized addresses. This exploits the centralized nature of traditional CDN services, which, while essential for efficient content delivery, are susceptible to compromise.
What is DNS Manipulation?
Attackers target the system responsible for translating domain names (e.g., example.com) into IP addresses. By modifying DNS entries, they can redirect users to malicious websites masquerading as legitimate WebApps.
What is BGP Hijacking?
Attackers manipulate the routing tables that direct internet traffic between networks. By falsely advertising ownership of IP address ranges associated with dApp WebApps, they can reroute traffic intended for a WebApp to their own servers.
These attacks highlight a paradox: dApps, built on decentralized blockchain technology, often rely on centralized web infrastructure for accessibility and performance. This reliance introduces vulnerabilities that attackers exploit, undermining the decentralized ethos and compromising user trust.
Notable Web3 Hacks Triggered by Web2 Weaknesses
Curve Finance (August 2022)
- What happened: Attackers hijacked Curve’s DNS via their domain registrar, redirecting users to a malicious site.
- Impact: Over $600K was stolen.
- Root cause: DNS hijacking: a Web2 vulnerability, nothing to do with the smart contracts.
Balancer (September 2023)
- What happened: The frontend of Balancer was compromised via a malicious script.
- Impact: ~$238K was drained.
- Root cause: Frontend was manipulated to redirect users to attacker-controlled wallets.
The Solution
Enter Harmony, the innovative asset monitoring tool we designed to tackle these challenges head-on. Harmony is our proactive response to the evolving threats targeting the interface between web2 and web3 technologies. By focusing on guarding key web2 components, Harmony ensures that any malicious changes are swiftly detected and communicated to team members, enabling quick mitigation actions.

How Does It Work?
Harmony continuously captures snapshots of the web state, including DNS records and scripts integrated into dApp websites. By monitoring DNS records in real-time, Harmony detects any unauthorized modifications. It also scrutinizes the scripts embedded within dApp websites, watching for unexpected changes or additions that could introduce vulnerabilities or compromise user security. If any suspicious activity is detected, Harmony immediately notifies team members, empowering them to take swift and decisive action. For developers, this might look like investigating the source of the unauthorized changes, implementing security patches, or restoring from a secure snapshot.
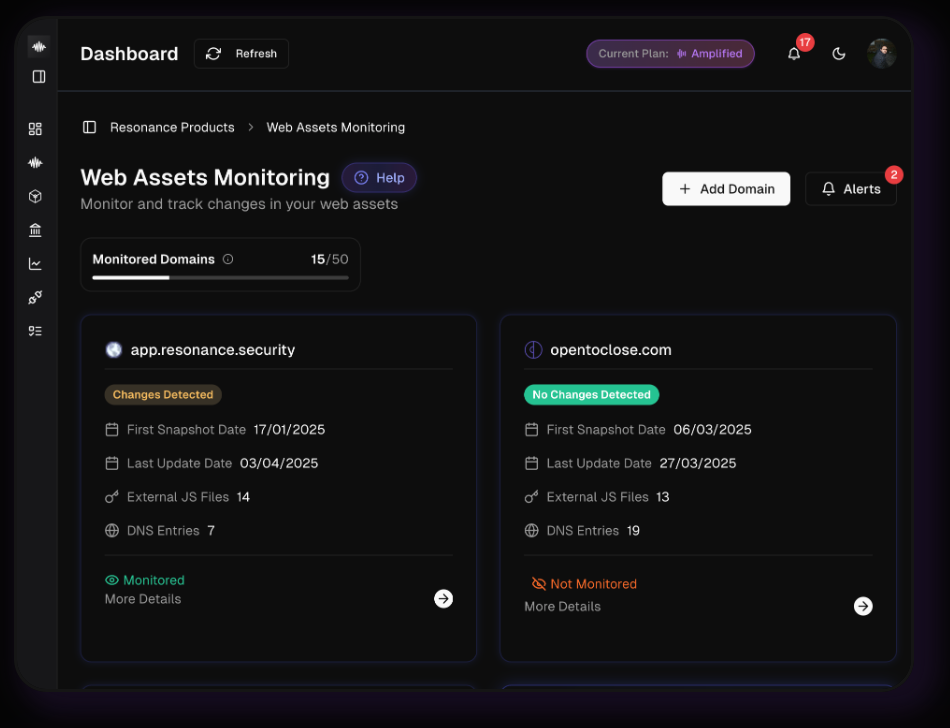
Harmony’s Broader Applicability
While Harmony was initially designed with dApps in mind, its hearty monitoring capabilities make it a valuable tool for all web2 applications. The same vulnerabilities that plague the web2 components of dApps, such as CDN hijacking, DNS manipulation, and BGP hijacking, can also affect traditional WebApps. Deploying Harmony allows web2 applications to also benefit from vigilant monitoring and rapid response mechanisms, ensuring their web components are secure against unauthorized modifications and potential threats.
Conclusion
As dApps continue to expand, their security becomes ever more critical. By monitoring the intersection of web2 and web3, Harmony provides a comprehensive solution to protect both decentralized and traditional applications. Users and developers can rest assured that their web components are under constant surveillance and protection. With Harmony, we can strengthen the defenses of the industry while continuing to foster growth and trust in both decentralized and traditional web technologies.
If you would like to check out how Harmony works and want a free demo of the same, then feel free to grab a 45-minutes slot with our security engineers.
















.png)